 |
Network Component
Version 7.19.0
MDK Middleware for IPv4 and IPv6 Networking
|
 |
Network Component
Version 7.19.0
MDK Middleware for IPv4 and IPv6 Networking
|
The Network Component offers secure software components that are using Mbed TLS. The user of the Network Component does not see the Mbed TLS API as it is hidden by the standard API of the secure component.
Currently, the following component is available in a secure variant:
To be able to communicate securely, you will need to generate appropriate certificates for the server. The section Creating your own certificates and keys explains how to achieve this for the secure components by using additional tools that are part of the Network Component.
The web server and the compact web server have secure variants available. In the Manage Run-Time Environment window simply select the appropriate variant:
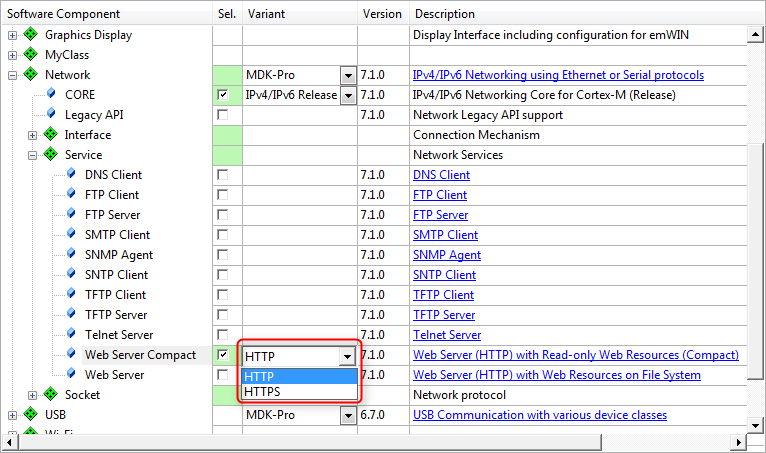
It is also possible to convert an already existing (compact) web server to a secure HTTPS web server. A few simple steps are required to achieve this:
Net_Security.c to the project which contains test keys/certificates. To change them, follow the steps provided in Creating your own certificates and keys.mbedTLS_Config.h configuration file with the following (a copy named mbedTLS_config_HTTPS.h is available in the Template folder): startup_xxx.s and set TLS_THREAD_STACK_SIZE in TLS_mbed.c (default is 4096)Net_Config_HTTP_Server.h):Net_Config.c file.The Network Component's HTTPS service adds the file Net_Security.c to the project. This file contains generic test keys/certificates which enable the application to run out of the box. If you want to adapt the keys/certificates to your needs, you can do this by modifying this file or by executing the batch file Net_Security.bat that is part of the Network Component.
Net_Security.bat can be registered in µVision under Tools for general usage:
$PRTE\Network\Net_Security.bat $PRTE\Network @K This setting is needed only once in µVision and will work for any project since it uses project related folders.
The file Net_Security.bat is copied to the project (.\RTE\Network) folder together with Net_Security.c. As it is project specific, the batch file can be customized to reflect your specific values for the certificates:
The beginning of the file contains some environment settings that can also be changed:
As soon as you run the batch file from the Tools menu, it will create the keys/certificates and change the Net_Security.c automatically to reflect the changes. You can then continue building the project.
Code example:
Server.key
Net_Security.c
The e-mail client is available in a secure variant. In the Manage Run-Time Environment window, simply select the appropriate variant:
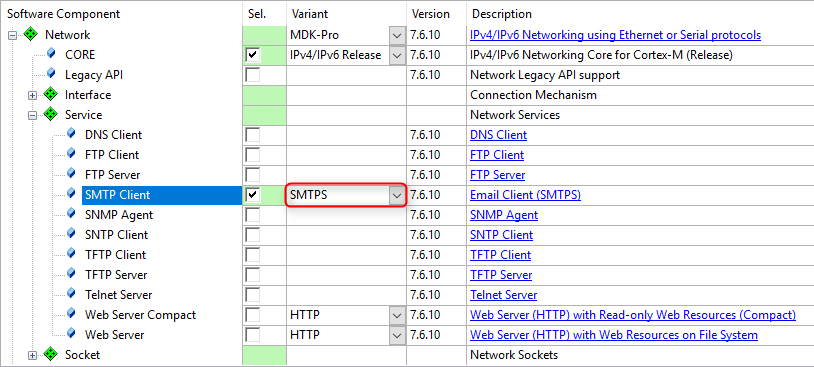
It is also possible to convert an already existing e-mail client to a secure SMTPS e-mail client. A few simple steps are required to achieve this:
Net_Security.c to the project which contains an empty CA certificate. To define it, follow the steps provided in Adding server root CA certificate.mbedTLS_Config.h configuration file with the following (a copy named mbedTLS_config_SMTPS.h is available in the Template folder): startup_xxx.s and set TLS_THREAD_STACK_SIZE in TLS_mbed.c (default is 4096)The SMTPS service of the Network Component adds the Net_Security.c file to the project. This file contains an empty section for the e-mail server root CA certificate, so you cannot initially build the application. You must provide a valid root CA certificate for the server that you use to send e-mail. The certificate must be provided in PEM-encoding. Copy the contents of the certificate into the NetSecurity_EmailServerCA structure in Net_Security.c and add a leading " and a trailing \n" to each line.
Verifying the e-mail server is required by default to increase e-mail security. If you do not want to verify the server, you can disable server verification by defining the SMTPS_SERVER_VERIFY_NONE in your project (Options for Component Class Network - SMTP_Client - C/C++ Preprocessor Symbols - Define).